Learn how to avoid SQL injection attacks with actionable strategies. Our guide offers expert tips to protect your applications and secure your data.

Picture this: it’s late on a Tuesday, your QA team is wrapping up a test run, and a developer types a single quote (') into a search bar. The entire application crashes, spitting out a raw database error. This isn’t a hypothetical scenario; it’s a real-world story of how a promising startup nearly lost everything to a simple SQL injection vulnerability. An attacker could have used that same flaw not just to crash the site, but to steal customer data, wipe the database, or take over the server.
SQL injection happens when an attacker tricks your application into running malicious database commands by sneaking them into user inputs like forms or URL parameters. This guide is designed to help product and development teams avoid SQL injection attacks with practical, actionable advice. We’ll skip the dense academic theory and focus on real-world strategies and tools you can implement today to protect your code, your data, and your users.
SQL injection remains one of the most stubborn and damaging security threats, topping vulnerability lists year after year. It all boils down to a single, common mistake: blindly trusting user input. Whenever an application takes data from a form, URL, or API call and plugs it directly into a database query, it swings the door wide open for an attack.
The fallout can be devastating. A simple coding oversight can quickly escalate into a full-blown security crisis, leading to massive data breaches that impact millions. You only have to look at high-profile incidents like the MOVEit SQL injection breach to see the catastrophic consequences.
The numbers don't lie. In 2023 alone, around 2,264 SQL injection vulnerabilities were discovered in open-source projects, and that number continues to climb. You can dig deeper into these SQL injection trends and statistics to understand just how widespread this issue is.
If SQL injection is so well-known, why is it still such a common problem? From my experience working with dev teams, it usually boils down to a few key reasons:
The core issue is beautifully simple: any data that originates outside your application must be treated as untrusted. Forgetting this is like leaving your front door unlocked and hoping for the best.
Understanding this fundamental risk is the first step for any team that wants to build secure, reliable software. Now, let's look at the real-world impact before diving into the specific defensive strategies you need to put in place.
It’s the kind of scenario that keeps engineering leaders up at night. One vulnerable line of code mushrooms into a catastrophe—a multi-million dollar disaster of regulatory fines, recovery costs, and a permanent black eye on customer trust. The path from a simple coding mistake to a public relations nightmare is often shockingly fast, which underscores just how critical it is to avoid sql injection attacks from day one. This isn't just about fending off an attack; it's about safeguarding your company's future.
Let’s get real for a moment. This isn't just theoretical. Think back to the "ResumeLooters" hacking campaign in 2023. Attackers exploited a straightforward SQL injection flaw across 65 different recruitment websites, walking away with the personal records of over 2 million job seekers. In a similar vein, Nokia suffered a breach when a related vulnerability exposed over 7,622 employee records.
These aren't just headlines; they're cautionary tales for every dev team. The damage isn't just the immediate financial hit, but the long-term erosion of your brand. As businesses scramble to keep up, Gartner predicts that worldwide spending on information security will climb to an eye-watering $212 billion. You can dig deeper into these widespread injection attack campaigns and their financial impact to see just how common this is.
What we're seeing is a classic cascading failure. The initial vulnerability is the crack in the dam, but the damage gets amplified by weak security protocols downstream. Once an attacker is in, they can often move laterally through a system, siphoning off far more data than they should have access to. All from one tiny mistake.
When a SQL injection attack succeeds, the financial bleeding is immediate, but the pain lasts for years. It’s crucial for product and development teams to grasp the full spectrum of costs, which extend far beyond just patching the broken code.
The expenses fall into two buckets: the obvious and the insidious.
Tangible Costs (The Obvious Ones):
Intangible Costs (The Silent Killers):
The true cost of a breach is never just the initial financial hit. It’s the slow, corrosive effect on your brand’s credibility and the massive opportunity cost of pulling your entire team off their mission to clean up a preventable mess. The most important strategies for any growing business must include ways to proactively avoid sql injection attacks, which you can start exploring on our use cases page.
Alright, let's get practical. Moving from theory to action is what separates a vulnerable application from a secure one. To effectively avoid sql injection attacks, you need to build defenses at multiple levels, from the code you write to how you manage the database itself.
Think of it as layered security. No single tactic is foolproof, but when you combine them, you build a formidable wall. Here are the core techniques I've seen work time and again in real-world applications.
If you take only one thing away from this guide, let it be this: use parameterized queries. Seriously. Also known as prepared statements, this single practice is the gold standard for stopping SQL injection and should be a non-negotiable rule in your codebase.
Instead of manually stitching user input into a query string—a recipe for disaster—you create a query template with placeholders. The database compiles this template first, locking down its structure and logic. Only after that compilation step does it safely slot the user's input into the placeholders. It treats that input purely as data, never as executable code.
This strict separation is the magic bullet. It prevents the database from ever confusing malicious input with a legitimate command, which completely neutralizes the attack. The entire vulnerability hinges on the database misinterpreting user input as part of the SQL command, and parameterization slams that door shut.
Stored procedures—pre-compiled SQL scripts saved in the database for reuse—are often mentioned as a security tool. And while they are great for organizing database logic, they are not a silver bullet against SQL injection. I've seen teams get this wrong.
The danger lies in how they are written. If you build dynamic SQL strings inside a stored procedure by concatenating inputs, you're right back at square one, just as vulnerable as before.
I once consulted for a startup whose team relied heavily on stored procedures, believing they were inherently secure. It turned out one of their key procedures was just mashing a search term into a query string, leaving a massive hole an attacker could drive a truck through. The lesson? Use stored procedures for clean architecture, but make sure they use parameterization internally. Otherwise, they offer a false sense of security.
While parameterization protects your database, you still need to be the bouncer at the front door of your application. That means validating every single piece of data that comes in. Your app should have strict rules for what it accepts and reject anything that doesn't fit the bill.
For example, on a user profile form, an attacker might try to submit a malicious script as their username. Even if a parameterized query stops an immediate SQL injection, that toxic data could get saved to the database. Later, when it’s displayed on a page, it could trigger a completely different kind of attack, like Cross-Site Scripting (XSS).
This is where whitelisting is your best friend. Instead of trying to create a blacklist of all the "bad" characters you can think of (a game you will always lose), you define a strict list of what's allowed.
This chart shows just how much more effective this approach is.
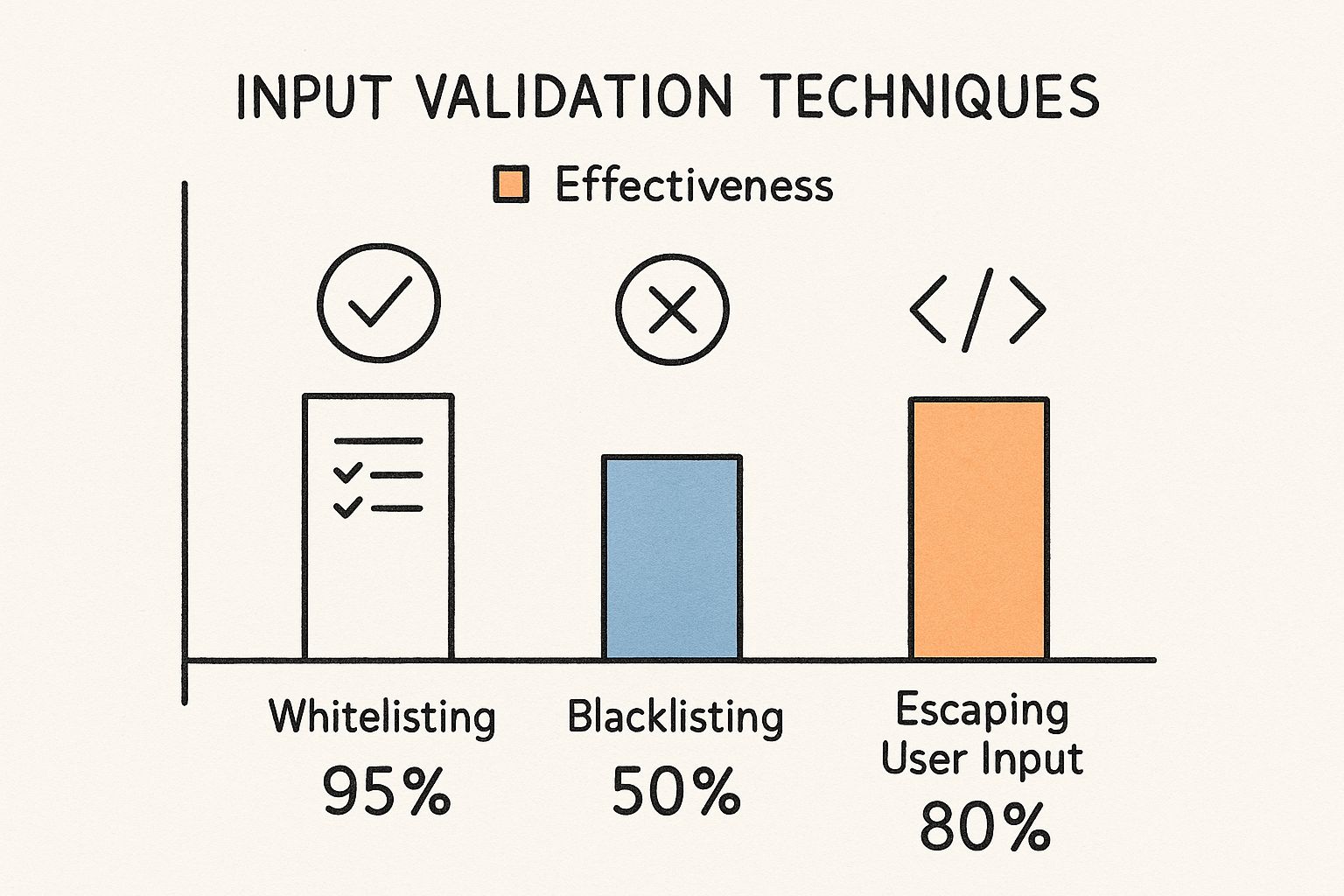
As you can see, whitelisting is the clear winner. Blacklisting is full of holes that clever attackers know how to exploit. While coding practices are key, they fit into a broader security posture, as covered in helpful guides like Mastering Security for WordPress Sites.
Choosing the right defense can feel overwhelming, but it's easier when you see them side-by-side. This table breaks down the main strategies to help you decide which to apply and when.
Each of these has its place, but a strong defense-in-depth strategy will use several of them together. Parameterization is your core defense, validation is your gatekeeper, and least privilege is your safety net.
You have to code with the assumption that, one day, an attacker might find a way through your defenses. The Principle of Least Privilege (PoLP) is your damage control plan for when that happens. The rule is simple: any user, program, or process should only have the bare-minimum permissions it needs to do its job, and nothing more.
Your web application should never connect to the database with an administrator account. That’s like giving an intruder the master key to your entire building. If they find one unlocked window, they can go anywhere they want.
Instead, create a dedicated database user for your application with locked-down permissions.
SELECT permissions on the necessary tables.ALTER, DROP, or CREATE tables. Those actions should be reserved for migrations run by a privileged user.This containment strategy is a vital part of a defense-in-depth security model. It won't stop an attack on its own, but it can turn a potential catastrophe into a much smaller, manageable incident. These are the kinds of foundational strategies we cover in our guide to software development security best practices.
Relying on modern development stacks can make teams feel secure, but it's easy to fall into a false sense of safety. One of the most common myths I’ve seen trip up even experienced developers is the belief that using an Object-Relational Mapping (ORM) tool automatically makes you invincible to SQL injection.
While tools like SQLAlchemy or the Django ORM are fantastic, they aren't a magic shield. They’re a huge step in the right direction, but true security comes from understanding how they work—and where they can fail.

This is where we go beyond the basics and really dig into how to avoid sql injection attacks in a modern, automated development pipeline. It’s all about knowing your tools inside and out, respecting their limitations, and layering your defenses with automated security checks.
ORMs are brilliant because they let you interact with your database using the objects and methods of your programming language, abstracting away the need to write raw SQL. This is their primary defense against injection vulnerabilities. Under the hood, they build safe, parameterized queries, so you don't have to sweat the small stuff.
But here’s the catch: nearly every ORM has an "escape hatch." It's a way to execute raw SQL for those complex or highly optimized database operations where the ORM’s abstractions just don't cut it. This is where the danger creeps right back in.
If a developer uses a raw query function and falls back on old habits like string formatting, the application becomes just as vulnerable as if it had no ORM at all.
For instance, say a developer using Django's ORM needs to run a very specific search. They might be tempted to do something like this:
from django.db import connection
def unsafe_user_search(search_term):
# This f-string opens the door wide open for an attack
query = f"SELECT * FROM users WHERE username = '{search_term}'"
with connection.cursor() as cursor:
cursor.execute(query)
return cursor.fetchall()
That f-string right there completely bypasses the ORM's built-in protections. It’s a classic SQL injection vulnerability, plain and simple.
The right way to do this is to let the database driver handle the user input safely, even when you're writing the SQL yourself.
from django.db import connection
def safe_user_search(search_term):
query = "SELECT * FROM users WHERE username = %s"
with connection.cursor() as cursor:
# The ORM's connection safely handles the parameter.
cursor.execute(query, [search_term])
return cursor.fetchall()
The key takeaway is simple: Treat any raw query execution with the same suspicion as writing SQL from scratch. Always use the parameterization features your ORM provides. No exceptions.
Even with impeccable code, you want another layer of defense. A Web Application Firewall (WAF) is like a security guard for your application, inspecting all incoming traffic before it even gets a chance to hit your code.
A WAF sits between your users and your server, filtering out malicious requests based on a set of rules. It’s trained to spot common SQL injection patterns—like suspicious uses of UNION SELECT or the classic ' OR 1=1—and block them on the spot. This provides a crucial layer of protection that can stop attacks from exploiting a vulnerability you didn't even know you had.
Here’s a good way to think about it:
Now, a WAF is a powerful tool, but it's not a silver bullet. Determined attackers can sometimes craft clever queries to bypass WAF rules. Your best bet is always a defense-in-depth strategy where a WAF and secure code work in tandem.
The cheapest and most effective way to fix a security bug is to prevent it from ever being deployed. This is where Static Application Security Testing (SAST) tools become an absolute game-changer. Think of SAST tools as automated expert code reviewers that plug right into your development workflow.
These tools scan your source code for known security anti-patterns before the code gets merged. They can automatically flag dangerous practices, like that unsafe raw SQL query we looked at, and report it directly in a developer's pull request. If you want to dive deeper, you can learn more about this process in our guide on what is static code analysis and how it fits into a secure workflow.
Integrating a SAST tool into your CI/CD pipeline creates an automated security gate that nothing gets past. At a startup I worked with, we implemented SAST and saw the number of security-related bugs reaching QA drop by over 60% in just three months. It completely shifted our culture from reactively fixing bugs to proactively preventing them. This is how you build resilient software at scale.
To build an application that can reliably avoid sql injection attacks, you need a holistic strategy. It starts with solid, secure coding habits, gets reinforced by perimeter defenses like a WAF, and is made scalable with integrated tooling like SAST.
Technical defenses are non-negotiable, but the most resilient organizations I've seen know that tools alone will never be enough. The absolute best strategy to avoid sql injection attacks is to build an engineering culture where security isn't an afterthought—it's just part of how you build software.
It’s all about shifting from a reactive mindset of frantically patching bugs to a proactive one of preventing vulnerabilities before a single line of code is even written. This cultural change doesn’t happen by accident. It requires a deliberate, sustained effort from leadership to weave security into the everyday fabric of the development lifecycle. This is how security becomes a shared responsibility, not just the job of a siloed team or a single "security person."
The real trick is to integrate security practices so seamlessly that they become muscle memory. Instead of bolting on heavy, cumbersome processes that everyone hates, you need to embed security into the tools and rituals your team already uses every day. This simple shift drastically reduces friction and makes secure habits stick.
Here are a few practical ways I've seen this work wonders:
I once worked with a product team that was constantly drowning in security tickets. Their agile sprints were always getting derailed by urgent, high-priority bugs that the QA team found late in the cycle. The engineers were completely burnt out, feeling like they were on a treadmill, just reacting to problems instead of building cool new features.
The engineering lead knew something had to change. They started small by adding a security review step to their sprint planning. Before the team estimated any new story, they spent just five minutes discussing potential security angles. "Where does this data come from? How will we validate it? What's the worst-case scenario if someone abuses this feature?"
This simple change had a profound impact. By forcing the team to think about security at the very beginning of the process, they started designing more resilient features from the ground up.
They paired this with a revamped code review process where secure coding patterns were actively celebrated. Senior engineers would leave positive comments on PRs that showed off great security practices, which reinforced the behavior they wanted to see. In just two quarters, they saw a 70% reduction in security-related tickets. The QA team could finally focus on more complex bugs, and the engineers got ahead of their technical debt.
Ultimately, building a security-first culture is about empowering every single developer to be a security champion. It requires giving them the knowledge, the tools, and—most importantly—the time to actually prioritize it.
When security becomes a shared value, it transforms from a burdensome checklist item into a point of collective pride. This cultural foundation is what allows teams to not only avoid sql injection attacks but to build a fundamentally stronger, more reliable product. It's the human layer of your defense, and it's often the most powerful one you have.
So, where do you go from here? If you walk away with anything, let it be these three rules. They are the bedrock of defending against SQL injection.
First, make parameterized queries your default, no-exceptions-allowed standard for talking to the database. Second, treat all user input as if it's actively trying to break your system—validate everything. And third, operate on the principle of least privilege. This simple rule can be the difference between a contained incident and a full-blown disaster.
The real shift happens when you stop seeing security as a roadblock and start treating it as a core product feature. This is what separates fragile applications from truly resilient ones. It’s how you build real, lasting trust with your users and, frankly, how you build a better product.
Security shouldn't be a last-minute checklist item; it has to be woven into the fabric of your development process. If you're curious how modern QA tools help create this kind of proactive security culture, this comparison of different platforms is a great place to start.
The most critical takeaway is this: A proactive, security-first culture is your single greatest defense. It turns every developer into a security champion and every code review into a security checkpoint.
The next move is yours. Start bringing automated security testing into your workflow and make that "security-first" mindset a real, tangible part of how you build software.
Ready to see how you can ship more secure code, faster? Start your free Sopa trial today and take the first step to bulletproof your applications.
Even with a solid plan, questions are bound to pop up when you're working to avoid SQL injection attacks. Let's run through some of the most common ones I hear from developers and product managers to clear up any lingering confusion.
This is a big one. While ORMs (Object-Relational Mapping tools) like SQLAlchemy or TypeORM are a massive step in the right direction, they aren't foolproof. Their biggest win is that they abstract away the need to write raw SQL, which dramatically cuts down your risk.
But here's the catch: almost every ORM has an "escape hatch"—a feature that lets you run raw SQL for those tricky, complex queries. The moment a developer uses that feature and slips back into old habits, like string concatenation with user input, you're right back in the danger zone.
The takeaway: Stick to the ORM's built-in, safe methods for filtering. If you absolutely must write a raw query, treat it with the same respect you'd give handwritten SQL and always use parameterization. No exceptions.
If you do only one thing, do this: use Parameterized Queries. You'll also hear them called Prepared Statements. This is hands-down the most effective, universally recommended defense.
It works by drawing a hard line between your SQL command and the data you're plugging into it. First, the database engine receives and compiles the SQL query template, complete with placeholders. Only after that step does it safely slot the user-supplied data into those placeholders.
This simple separation ensures the database treats user input as just data, never as code to be executed. It completely defuses the core of an SQL injection attack. Other layers like input validation are vital, but parameterization is the bedrock of your defense. To see how this fits into the bigger picture, check out how Sopa can help secure your entire development lifecycle.
There's no single magic test; you need to attack this from a few angles.
First up is good old-fashioned manual code review. You have to get your eyes on the code and hunt for any place where user input is being stitched directly into a SQL query string. It's tedious, but necessary.
Next, bring in the machines. Automated tools are your best friend here.
Finally, for the most comprehensive check, you'll want to do penetration testing. This is where you bring in a security pro to ethically try and break your application. It’s the ultimate reality check. Of course, integrating a tool like Sopa can automate a huge chunk of this testing and embed it right into your team's workflow.
Ready to stop shipping vulnerabilities and start building more resilient applications? With Sopa, you can automate your code reviews to catch security risks like SQL injection before they ever reach production.
Start your free Sopa trial today and see how easy it is to ship secure, high-quality code.
