Discover what is static code analysis and how it helps developers write secure, high-quality code. Learn practical benefits in this informative guide.

Ever wish you had an automated expert on your team, one that could proofread every line of code for bugs, security risks, and style mistakes before it even runs? That’s exactly what static code analysis is: a proactive checkup for your software. It analyzes your source code the moment it's written—that’s the ‘static’ part—acting as your first line of defense against costly errors and saving your team from future headaches.

Let's break it down with a simple story. Imagine a startup is building a new mobile banking app. Their lead architect reviews the blueprints for the app's security features long before any construction begins. By studying the plans, she spots a design flaw that could potentially expose user data. That's precisely what static analysis does for your software—it finds problems at the blueprint stage.
This is a world away from dynamic analysis, which is more like stress-testing the finished app by trying to hack into it after it's been built. That's still critical, but it happens much later. Catching a problem in the blueprint is always cheaper and faster than fixing a security breach in a live application.
To give you a clearer picture, here's a quick rundown of what static code analysis brings to the table for any product or development team.
This table breaks down the essentials of what static code analysis is all about in practical terms.
Ultimately, static analysis acts as an automated quality gate, embedding essential checks directly into your team's daily workflow.
A good way to think about a static analysis tool is as a super-diligent member of your development team. It reviews every single line of code, never gets tired, and never forgets the rules you've set. It’s your team's automated guardian, systematically scanning the codebase against a predefined set of rules to flag potential issues.
These rules aren't just about picky formatting; they cover a wide range of concerns that are vital for any modern development team:
By automating this first line of defense, static analysis frees up your developers from the tedious parts of manual code reviews. Instead of hunting for simple mistakes, they can focus their expertise on the more complex architectural and business logic decisions.
You’ll often hear the term "shifting left" in software development circles. It simply means moving quality and security checks as early as possible in the development lifecycle. Static analysis is the poster child for this practice.
When you integrate it directly into a developer's workflow—right inside their code editor or as part of every commit—it provides immediate feedback. This instant feedback loop is incredibly powerful. Imagine a developer getting a security alert as they type, allowing them to fix a vulnerability in seconds. This prevents sloppy or vulnerable code from ever making its way into the main codebase in the first place.
For product and development teams, the benefits are huge: fewer bugs reach the QA stage, development cycles get shorter, and the final product is inherently more secure. A key step in getting this right is learning how to compare different static code analysis tools to find the best fit for your team. At the end of the day, it's about building an intelligent safety net that helps your team ship better software, faster.
Ever wondered what's really happening when a static analysis tool scans your code? It’s not magic. Think of it as a highly skilled architect who, instead of just looking at a building, creates a detailed 3D model to understand its core structure, plumbing, and electrical systems.
The tool doesn't just read your code line by line. It actually transforms it into a structured model that reveals the logic and data flow beneath the surface. This gives it a bird's-eye view of your entire codebase, letting it spot connections and potential problems that a human reviewer might easily overlook. This deep, structural understanding is what makes static code analysis so powerful.
The very first thing a static analysis tool does is parse your code. It breaks everything down into its grammatical parts and builds an internal representation, most commonly an Abstract Syntax Tree (AST). An AST is essentially a map of your code’s structure.
Let's take a simple line of code: user_id = 10;. The AST would represent this as a tree with an "assignment" node at the top. Branching from that node would be two children: one for the variable user_id and another for the integer value 10. This tree makes it incredibly simple for the tool to see the relationships between different pieces of code.
For more complex analysis, the tool might build other models, too:
By combining these models, the tool creates a comprehensive blueprint of your entire codebase. It’s this blueprint, not the raw text you wrote, that gets analyzed.
Once the blueprint is built, the real work begins. The tool runs its model against a massive library of predefined rules. Each rule is designed to find a specific type of problem, from minor style issues to critical security vulnerabilities.
It's like having an automated code review checklist on steroids. The tool never gets tired, never gets distracted, and methodically checks every single line against thousands of known bad practices.
Here's a classic real-world example. A junior developer writes a simple database query:
query = "SELECT * FROM users WHERE name = '" + user_input + "';"
The static analysis tool’s AST immediately sees that user_input, which comes from an external source, is being stitched directly into a SQL query string. The rules engine instantly flags this pattern as a textbook SQL injection vulnerability. The tool doesn't need to execute the code to know this is a huge security risk. The developer gets instant feedback and can fix it long before it ever gets into a pull request.
The infographic below illustrates how this entire process fits into the bigger picture of software development, helping with early bug detection, boosting code quality, and making code reviews much faster.
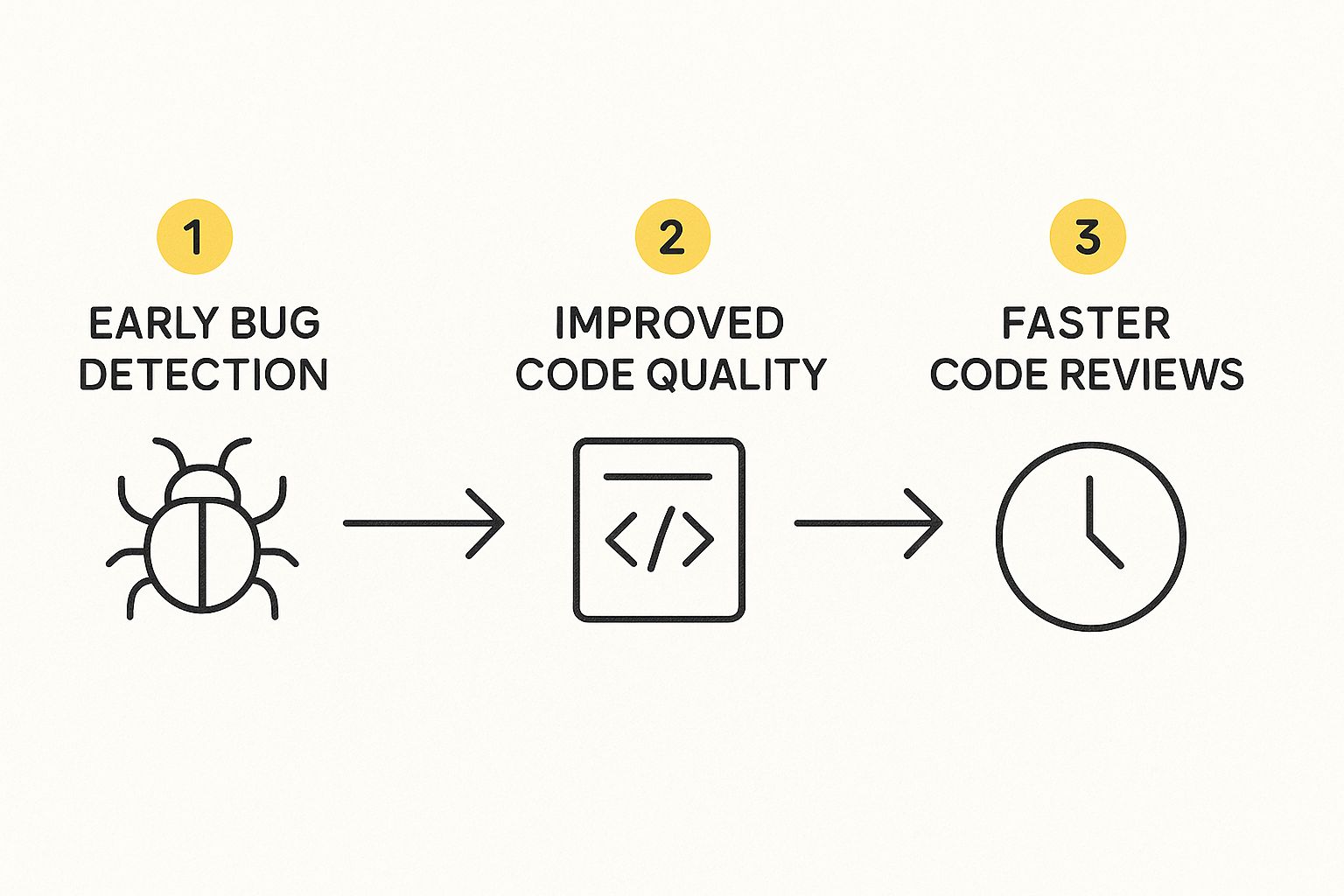
As you can see, catching problems at the earliest stage creates a ripple effect that benefits the entire development lifecycle. This is how automated analysis works to protect your codebase from the inside out. For any team serious about building secure and reliable software, adopting these tools is no longer a "nice-to-have"—it's a core part of the modern development workflow. If you're wondering which tool is right for you, check out our in-depth comparison of static analysis tools to find the perfect fit.
Understanding the mechanics of static analysis is one thing, but seeing its real-world impact is where things get interesting. For development and product teams, static code analysis isn't just a technical exercise—it's a game-changer that delivers real, measurable results. It fundamentally shifts the development process from a reactive, bug-fixing scramble to a proactive, quality-first workflow.
Here's a real-world story: a fast-growing startup was about to launch a huge new feature. During a final code review, their automated static analysis tool flagged a subtle but critical vulnerability in a pull request. If it had gone through, this tiny flaw could have exposed sensitive user data. By catching it automatically before the code was ever merged, the team dodged a potential data breach, saving themselves a world of trouble and protecting their reputation.
One of the first things teams notice is how much faster everything gets. Let's be honest, manual code reviews can be a major bottleneck. Developers end up spending hours spotting basic errors, style issues, and common mistakes—time that could be poured into building complex features and solving real problems.
Static analysis automates the grunt work. Think of it as a tireless assistant that handles the first pass of every review, instantly catching all the easy-to-spot issues.
This shift doesn't just make development faster; it makes it smarter. By handing off the tedious checks to a machine, your team can focus on what they do best: building great software. You can see how automation is changing the landscape by exploring our guide on other AI-powered code review tools.
As a team grows, keeping the codebase clean and consistent is a real challenge. Every developer has their own style, and without a clear process, things can get messy fast. A messy codebase is hard to navigate and even harder to maintain. Static analysis acts as the impartial referee for your team’s coding standards.
You define a shared set of rules, and the tool ensures every single line of code meets that quality bar before it gets checked in. This creates a predictable and healthy codebase that's built for the long haul. It also helps new team members get up to speed quickly, as the tool guides them toward best practices from their very first commit.
Static analysis tools create a single source of truth for code quality. They remove subjective arguments from code reviews and align the entire team around objective, measurable standards.
Perhaps the most critical benefit is the massive boost to security. Many of the most common and dangerous vulnerabilities—things like SQL injection and cross-site scripting (XSS)—follow predictable patterns. These are exactly the kinds of patterns that static analysis tools are built to find.
The impact here is huge. One recent report found that a staggering 72% of audited software vulnerabilities could be traced back to code defects that are easily detectable by static analysis. That number alone shows just how powerful these tools are at finding the root cause of security breaches before they can do any damage. For a closer look at how static analysis fits into a broader security strategy, particularly for APIs, check out this comprehensive guide on security testing of API endpoints, including SAST.
By embedding security checks right into the development pipeline, you make security everyone’s job, not just a task for a separate team. This "shift-left" approach is the key to building secure and resilient applications from the very beginning.
Picking the right static analysis tool can feel like a chore, but it doesn't have to be. The best tool isn't the one with a laundry list of features; it's the one that fits your team's workflow like a glove. What works for a Python data science team will likely be a terrible fit for developers building a mobile app in Java.
The real goal is to find a partner that slides right into your daily process, giving you clear, actionable feedback without getting in the way. Think of it like adding an automated expert to your team—you need one that speaks your language, plays well with your existing setup, and communicates without causing a fuss. Let's break down the key things to look for.
This is the absolute baseline. If the tool doesn't have rock-solid support for the programming languages and frameworks you use day-in and day-out, it's a non-starter. A tool that's brilliant for JavaScript is just dead weight if your team lives and breathes Go.
But don’t just think about today. What’s on your tech roadmap for the next year? Are you planning to adopt a new framework or language? Choosing a tool that supports your future plans will save you a world of hurt later on. While most modern tools boast wide support, the depth of that support can be a different story.
Even the most powerful tool is worthless if nobody uses it. For static analysis to actually make a difference, it has to become an invisible, helpful part of your development cycle. That means it needs to integrate smoothly with the tools your team already knows and loves.
Here are the must-have integrations:
Without these deep integrations, the tool is just another dashboard people have to remember to check, and its impact will plummet.
Not all static analysis tools are created equal when it to accuracy. The sweet spot is a tool that finds what matters but doesn't drown you in "noise" from false positives. A tool that screams about hundreds of non-issues on every scan will get ignored fast. We call this alert fatigue, and it’s a real problem.
A great static analysis tool should feel like a helpful signal, not a constant source of noise. Customization is key to tuning the tool to your team's specific context and priorities.
Look for tools that let you customize the rules. You should be able to turn off checks that are irrelevant to your project and tweak the severity of others. This control lets you tailor the feedback to focus on what actually matters, making every alert worth looking at.
To help you start sorting through the options, it helps to understand the main categories of static analysis tools. Each type is built for a different job and comes with its own set of trade-offs.
This table breaks down the different categories of static analysis tools, helping you decide which approach best fits your project's needs and budget.
Ultimately, choosing the right tool is a strategic decision. By carefully weighing language support, workflow integration, and that crucial balance between signal and noise, you can find a solution that helps your team ship better, more secure code. For a closer look, you can explore our detailed comparison of static code analysis tools to see how different options stack up.

The real magic of static analysis happens when it becomes an invisible, almost instinctual part of your development process. This isn't about adding another chore to a developer's plate. It’s about embedding automated quality checks so deeply that they feel like a natural extension of writing code.
The goal is to stop treating bug-fixing as a reactive fire drill and start making it a proactive, preventative habit. This is where Continuous Integration and Continuous Delivery (CI/CD) pipelines truly shine, creating a powerful feedback loop that turns developers into the first—and best—line of defense for code quality.
Your CI/CD pipeline is the perfect home for automated static analysis. Instead of crossing your fingers and hoping developers remember to run a scan, you can set it up to trigger automatically at the most crucial points. If you're new to the concept, understanding what CI/CD is and why it's needed is a great starting point, as these tools are designed to work hand-in-glove with modern pipelines.
Think of this automation as your personal quality gatekeeper. Here’s how it usually works:
This simple process ensures that sloppy or vulnerable code never even touches your main codebase. It’s a powerful way to enforce high standards of quality and security across your entire team.
Picture a small, fast-moving startup. They were stuck in a classic cycle: bugs were constantly slipping past developers and landing in QA's lap, leading to endless delays and frustrating rework. They decided to try something new and integrated a static analysis tool right into their GitHub workflow.
At first, the team was skeptical. The initial scan lit up like a Christmas tree, flagging hundreds of minor issues in their legacy code. It felt overwhelming. But instead of trying to boil the ocean, they took a smarter approach: they configured the tool to only fail a build if new critical issues were introduced.
The effect was immediate. Developers started getting feedback directly on their pull requests. They began catching and fixing small mistakes before even asking a teammate for a review. In just a few months, the number of bugs reaching QA plummeted by over 40%. They weren't just fixing bugs anymore; they were preventing them.
Just dropping a new tool on your team and hoping for the best is a recipe for frustration. A thoughtful rollout strategy is key to getting everyone on board.
Here are a few tips for a successful integration:
The goal is to make the tool a trusted part of the development process. When developers see it as something that helps them write better code faster, adoption becomes natural and enthusiastic.
The move toward DevSecOps has put this kind of proactive security into hyperdrive. In fact, the market for static code analysis software is expected to more than double from USD 1.2 billion in 2023 to around USD 2.6 billion by 2032. This growth is almost entirely driven by the push to embed security checks earlier and earlier in the development lifecycle.
Ultimately, bringing static analysis into your daily workflow is about building a culture of quality from the ground up. It gives your team the feedback they need to catch issues early, streamline collaboration, and ship better, more secure software with confidence.
So, what's the big takeaway? Static code analysis isn't just another tool to add to the pile; it's a fundamental shift in how modern software teams build high-quality products. It's about catching bugs early, shoring up your security defenses, and making collaboration smoother.
Ultimately, this saves a massive amount of time and money by stopping critical issues long before they ever see a production environment.
Think about how this fits into your larger quality strategy. Static analysis is a powerful first line of defense in a robust mobile app quality assurance program, flagging problems before code is even packaged for testing. When you understand concepts like what a pull request is, you can really see how these automated checks act as a crucial safety net for every single contribution.
The greatest value of static code analysis lies in its ability to transform quality from a final checkpoint into a continuous, proactive habit built directly into the developer workflow.
Now it’s time to move from theory to practice. The only way to truly appreciate the difference it makes is to see it in action on your own codebase. Sopa can help your team improve code quality and security without slowing you down.
Ready to see for yourself? Start your free trial of Sopa and see how automated code analysis can transform your development process.
When teams first start looking into static code analysis, a handful of questions pop up almost immediately. Getting a handle on the practical side of things—like telling different analysis types apart or figuring out what to do with all the results—is a big step. Here are some straightforward answers to the questions we hear most often.
Think of this as the practical advice you need to bring these tools into your workflow and actually make them stick.
This is probably the most common question, but the difference is actually pretty simple once you focus on when the analysis happens.
They aren't competing against each other; they're two sides of the same coin. Static analysis finds flaws in the blueprint, while dynamic analysis spots problems in the finished building. A solid quality strategy needs both.
For instance, a static analysis tool can spot a potential SQL injection vulnerability just by recognizing a risky code pattern. A dynamic tool, on the other hand, might catch a memory leak that only happens after a user has clicked a specific button a thousand times. Using a tool like Sopa, which focuses on static analysis, helps you catch problems at the earliest and cheapest stage.
Let's be honest: false positives are a fact of life with static analysis. A tool might flag something that isn't really a problem, and if that happens too often, developers start tuning out the alerts completely. We've all seen it happen.
The trick is to stop thinking of the tool as a strict judge and start treating it like a smart assistant you can train.
Here’s a practical game plan:
By actively managing the configuration, you can cut down the noise so that every alert your team sees is one they should actually pay attention to.
This question gets to the heart of a huge issue today: software supply chain security. The short answer is that traditional static analysis tools are built to look at the source code you write, not the compiled code you pull in from a third-party library.
But there's a related practice called Software Composition Analysis (SCA) that does exactly that. SCA tools scan all your project's dependencies and check them against databases of known vulnerabilities (like the CVE list). If you're using a library with a known security flaw, SCA will let you know.
Many modern security platforms now bundle SAST (static analysis) and SCA together to give you the full picture. So while a pure static analysis tool might not scan the library's code directly, it can see how your code interacts with it and flag unsafe patterns. It's a powerful one-two punch for securing both your own code and your dependencies. For a closer look at how different tools tackle this, check out our detailed tool comparison page.
Ready to see how automated analysis can completely change your code review process? With Sopa, you can catch bugs and security risks long before they have a chance to reach production. Start your free trial and discover a smarter, faster way to ship great code.
